Windows 10 Persistence via PATH directories - CDPSvc
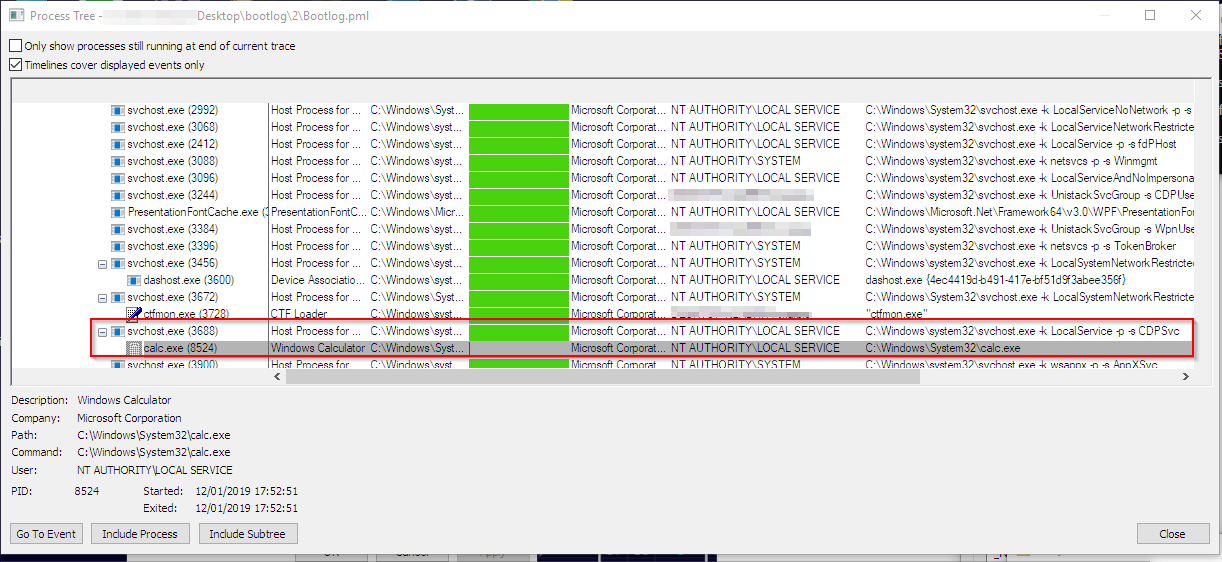
TL;DR: CDPSvc searches the file cdpsgshims.dll inside PATH directories and loads it if found.
CDPSvc is the Connected Devices Platform Service, enabled by default under Windows 10 (since 1607). If an attacker is able to write in any directory specified in the system PATH, this allows to persist on the system as NT AUTHORITY\LocalService.
The issue is not considered a security-vulnerability, but rather a security-relevant misconfiguration. With a default Windows installation, there can’t be a non-admin directory in the PATH, so this can’t be exploited.
Download:
A sample DLL (source included) that executes calc.exe is available here: CDPSvcPersist
 marpie
marpie
 @markus_pieton
@markus_pieton